Vulnerability statistics for 2012
 Dear users of Find-XSS.net! In this section we offer you to get acquainted with the statistics obtained by scanning our clients’ projects.
Dear users of Find-XSS.net! In this section we offer you to get acquainted with the statistics obtained by scanning our clients’ projects.
Note: we present data for the last two years below.
A new version of 0.5.0 scanner and how to use it
 As it was promised earlier, the status of Warning as well as the status of Error is abolished in a new version of a scanner. Scan report in the new version has changed a lot. Now the report specifies three types of vulnerabilities: XSS, SQL injection and Active script (other vulnerabilities). Scan report in previous versions of the scanner put some in a deadlock, especially vulnerability to the status of Warning. In the new version of scanner everything is done to simplify the understanding of the logic on which the scanner has found a particular vulnerability. The report shows the key lines of code side by side with the vulnerability line. Therefore, we can trace all the chain the scanner used in the analysis. Unsafe option is released in red in the report. For non-experienced website owners, when you hover the mouse on a line with a vulnerability, the prompt with the way to remove appears.
As it was promised earlier, the status of Warning as well as the status of Error is abolished in a new version of a scanner. Scan report in the new version has changed a lot. Now the report specifies three types of vulnerabilities: XSS, SQL injection and Active script (other vulnerabilities). Scan report in previous versions of the scanner put some in a deadlock, especially vulnerability to the status of Warning. In the new version of scanner everything is done to simplify the understanding of the logic on which the scanner has found a particular vulnerability. The report shows the key lines of code side by side with the vulnerability line. Therefore, we can trace all the chain the scanner used in the analysis. Unsafe option is released in red in the report. For non-experienced website owners, when you hover the mouse on a line with a vulnerability, the prompt with the way to remove appears.
Vulnerability statistics for 2011
 The year of 2011 has ended and it is possible to collect and analyze data. When scanning, the scanner logs size of a file, the number of discovered vulnerabilities, there is a counter of scans as well.
The year of 2011 has ended and it is possible to collect and analyze data. When scanning, the scanner logs size of a file, the number of discovered vulnerabilities, there is a counter of scans as well.
Here are the figures for 2011:
The number of scans 13.143, the amount of trusted code 7,122,421,827 bytes, the number of discovered vulnerabilities 35.545.
If you make simple mathematical operations you’ll take 2.7 vulnerability for each scanning. Or, in other words, one vulnerability on every 200.377 bytes of code.
The site MySQL.com has been hacked

If you have already read our funny and absurd story you may have noticed that we didn’t mention any names. The heroes of the today’s news, on the other hand, are probably well known to the whole world. Some Romanian hackers TinKode and Ne0h hacked the MySQL.com and Sun.com sites. Moreover, the hacking was performed by means of that very SQL Injection which our website is specifically meant to fight!
Thanks to this vulnerability the hackers obtained a list of databases and table contents used by this source as well as the tables containing users’ info – their logins and passwords.
Furthermore, already in January an XSS- vulnerability had already been discovered in the authoritative MySQL.com website, which made it possible to attack the site by using the cross-site scripting.
What is XSS?
 XSS is a term used to refer to one of the varieties of website vulnerabilities, i.e. when a culprit has a possibility to insert into such a site some foreign scripts which can later be performed on the client’s (victim’s) side. Notice that the victims may be not only users but also other severs or internet services. The abbreviation XSS is derived from Cross Site Scripting but in order to avoid confusion with CSS, which is widely known as Cascading Style Sheets, a different abbreviation has been adopted.
XSS is a term used to refer to one of the varieties of website vulnerabilities, i.e. when a culprit has a possibility to insert into such a site some foreign scripts which can later be performed on the client’s (victim’s) side. Notice that the victims may be not only users but also other severs or internet services. The abbreviation XSS is derived from Cross Site Scripting but in order to avoid confusion with CSS, which is widely known as Cascading Style Sheets, a different abbreviation has been adopted.
Programmers have not paid proper attention to XSS for a long time, since they were not considered dangerous. But due to the rapid development of web-technologies, this vulnerability has become a real plague for the internet community. That is why a classification of XSS vulnerabilities has already appeared today, both according to the mechanism of attack execution and according to the channels of script insertion.
How does it work?
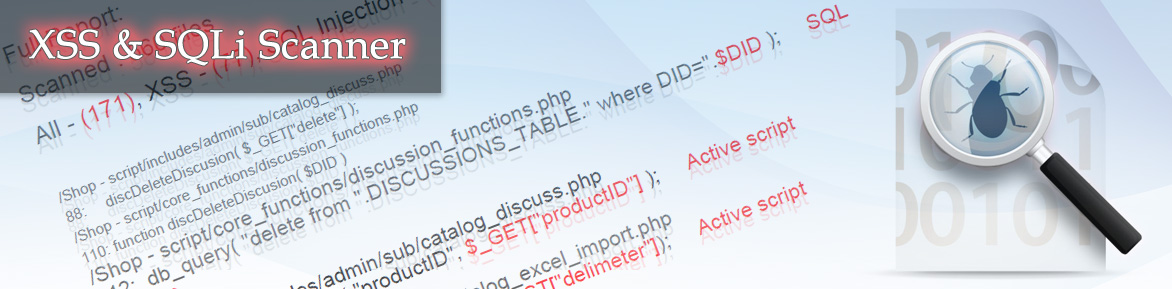
 This tool is designed to help search for XSS and SQL Injection vulnerabilities. This service enables you to check PHP files as well ZIP archives up to 10 mb. The VIP users ( registered users) are provided with a detailed scan report. As a result of the scanner’s work, the name of the file will show up in which a potential vulnerability has been found as well as numbered lines of the insecure code in that file, a vulnerable parameter and the vulnerability type.
This tool is designed to help search for XSS and SQL Injection vulnerabilities. This service enables you to check PHP files as well ZIP archives up to 10 mb. The VIP users ( registered users) are provided with a detailed scan report. As a result of the scanner’s work, the name of the file will show up in which a potential vulnerability has been found as well as numbered lines of the insecure code in that file, a vulnerable parameter and the vulnerability type.





 Scanner
Scanner
