 XSS is a term used to refer to one of the varieties of website vulnerabilities, i.e. when a culprit has a possibility to insert into such a site some foreign scripts which can later be performed on the client’s (victim’s) side. Notice that the victims may be not only users but also other severs or internet services. The abbreviation XSS is derived from Cross Site Scripting but in order to avoid confusion with CSS, which is widely known as Cascading Style Sheets, a different abbreviation has been adopted.
XSS is a term used to refer to one of the varieties of website vulnerabilities, i.e. when a culprit has a possibility to insert into such a site some foreign scripts which can later be performed on the client’s (victim’s) side. Notice that the victims may be not only users but also other severs or internet services. The abbreviation XSS is derived from Cross Site Scripting but in order to avoid confusion with CSS, which is widely known as Cascading Style Sheets, a different abbreviation has been adopted.
Programmers have not paid proper attention to XSS for a long time, since they were not considered dangerous. But due to the rapid development of web-technologies, this vulnerability has become a real plague for the internet community. That is why a classification of XSS vulnerabilities has already appeared today, both according to the mechanism of attack execution and according to the channels of script insertion.
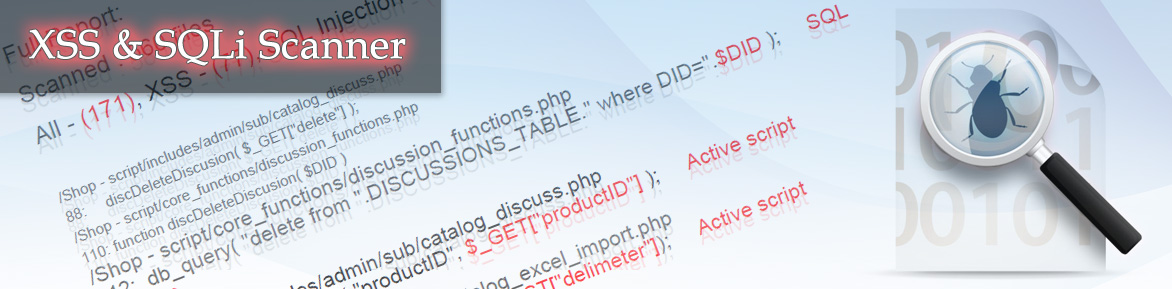
Let’s take an example of an attack using the XSS vulnerability. Let’s imagine that the culprit used this kind of vulnerability and as a result the visitors of the site saw a full screen sign “Johnny has visited here!” or something uglier. If we are talking about a serious project this may negatively affect the reputation of the business and its clients’ trust. But this is just a petty mischief compared with those attacks which result not only in stealing data from clients but even gaining possession of the Administrator’s access! Another illustration could be the so called DoS attack (Denial of Service), which causes a site to slow down or altogether switches off the displayed contents in the user’s browser.
The culprit’s imagination is unlimited. Every day he invents new more sophisticated methods of hacking sites by using XSS vulnerabilities. Don’t allow the culprits to anticipate you! Use an adequate weapon in the war against them – our scanner find-xss.net!
Article





 Scanner
Scanner
