The question of trust: a Find-Compromise scanner client
 Are you afraid to download the source code in the scanner? We understand you but now you should not worry about it. We have developed a client part of scanner. It works in Java. So if you have not installed the Java virtual machine yet, it’s the time to do it. A Find-Compromise Client will analyze your project on your computer and create a file. The file will have pieces of code which require additional testing, by the server part of the scanner now. After downloading of this file the scanner will give the report. So you will not have to worry about your project, and we - for exclusivity of our product.
Are you afraid to download the source code in the scanner? We understand you but now you should not worry about it. We have developed a client part of scanner. It works in Java. So if you have not installed the Java virtual machine yet, it’s the time to do it. A Find-Compromise Client will analyze your project on your computer and create a file. The file will have pieces of code which require additional testing, by the server part of the scanner now. After downloading of this file the scanner will give the report. So you will not have to worry about your project, and we - for exclusivity of our product.
Comprehensive protection of site by find-xss.net tools
 Currently we can provide four utilities for finding vulnerabilities, as well as scanner of PHP code for XSS, SQL injection and other vulnerabilities.
Currently we can provide four utilities for finding vulnerabilities, as well as scanner of PHP code for XSS, SQL injection and other vulnerabilities.
This is a list of utilities:
Find-Date - searching shells filled to site by an attacker.
Find-Port - checking open ports.
Find-Info - utility for checking folders and files rights.
Find-Error - mass files checking for syntax errors.
Each of the utilities makes not big but important contribution to the detection of errors and vulnerabilities. It is recommended to use each of them. The more so that they are easy to use and do not require much time or great knowledge.
Статусы Error и Warning в версии 0.4.7
 Уважаемые пользователи Find-XSS.net, обращаем Ваше внимание на то, что с совершенствованием алгоритма XSS-сканера постепенно изменяется и смысл присваиваемых им статусов. Так, в начальных версиях сканера присутствовал статус Notice, предупреждавший пользователя о существовании возможной опасности. Несмотря на тот факт, что 50% случаев этим предупреждением можно было пренебречь, в последующих версиях сканер стал отслеживать все, что касалось этого статуса. Поэтому мы приняли решение упразднить Notice, оставив только статусы Error и Warning. В предлагаемой Вам обновленной версии (0.4.7) сканера и статус Error, и статус Warning означают наличие уязвимости. Разница между ними заключается лишь в том, что статус Error определяет конкретный тип уязвимости: XSS, SQL injection или же какой-нибудь другой активный код; а статус Warning означает, что во время проверки сканер обнаружил уязвимость SQL injection или XSS в теле функции, и Вам нужно проверить как параметры, получаемые этой функцией, в указанной строке кода, так и их использование в теле функции.
Уважаемые пользователи Find-XSS.net, обращаем Ваше внимание на то, что с совершенствованием алгоритма XSS-сканера постепенно изменяется и смысл присваиваемых им статусов. Так, в начальных версиях сканера присутствовал статус Notice, предупреждавший пользователя о существовании возможной опасности. Несмотря на тот факт, что 50% случаев этим предупреждением можно было пренебречь, в последующих версиях сканер стал отслеживать все, что касалось этого статуса. Поэтому мы приняли решение упразднить Notice, оставив только статусы Error и Warning. В предлагаемой Вам обновленной версии (0.4.7) сканера и статус Error, и статус Warning означают наличие уязвимости. Разница между ними заключается лишь в том, что статус Error определяет конкретный тип уязвимости: XSS, SQL injection или же какой-нибудь другой активный код; а статус Warning означает, что во время проверки сканер обнаружил уязвимость SQL injection или XSS в теле функции, и Вам нужно проверить как параметры, получаемые этой функцией, в указанной строке кода, так и их использование в теле функции.
What is XSS?
 XSS is a term used to refer to one of the varieties of website vulnerabilities, i.e. when a culprit has a possibility to insert into such a site some foreign scripts which can later be performed on the client’s (victim’s) side. Notice that the victims may be not only users but also other severs or internet services. The abbreviation XSS is derived from Cross Site Scripting but in order to avoid confusion with CSS, which is widely known as Cascading Style Sheets, a different abbreviation has been adopted.
XSS is a term used to refer to one of the varieties of website vulnerabilities, i.e. when a culprit has a possibility to insert into such a site some foreign scripts which can later be performed on the client’s (victim’s) side. Notice that the victims may be not only users but also other severs or internet services. The abbreviation XSS is derived from Cross Site Scripting but in order to avoid confusion with CSS, which is widely known as Cascading Style Sheets, a different abbreviation has been adopted.
Programmers have not paid proper attention to XSS for a long time, since they were not considered dangerous. But due to the rapid development of web-technologies, this vulnerability has become a real plague for the internet community. That is why a classification of XSS vulnerabilities has already appeared today, both according to the mechanism of attack execution and according to the channels of script insertion.
What is an SQL injection?
 An SQL injection (or an insertion of an SQL code) is one of the most dangerous methods of site hacking. An SQL injection hacking is based on inserting an arbitrary SQL code into a request to the database. The most common reason for an SQL injection type of attack is an incorrect processing of the input data that is transferred into SQL requests. Suppose a server uses the input parameter id which is transferred through the GET line of the request type http://www.somesite.com/?id=123 to search the entry in the database table with the information about the user with the user_id which equals 123. Let’s also suppose that the PHP script responsible for the SQL request looks as follows:
An SQL injection (or an insertion of an SQL code) is one of the most dangerous methods of site hacking. An SQL injection hacking is based on inserting an arbitrary SQL code into a request to the database. The most common reason for an SQL injection type of attack is an incorrect processing of the input data that is transferred into SQL requests. Suppose a server uses the input parameter id which is transferred through the GET line of the request type http://www.somesite.com/?id=123 to search the entry in the database table with the information about the user with the user_id which equals 123. Let’s also suppose that the PHP script responsible for the SQL request looks as follows:
How does it work?
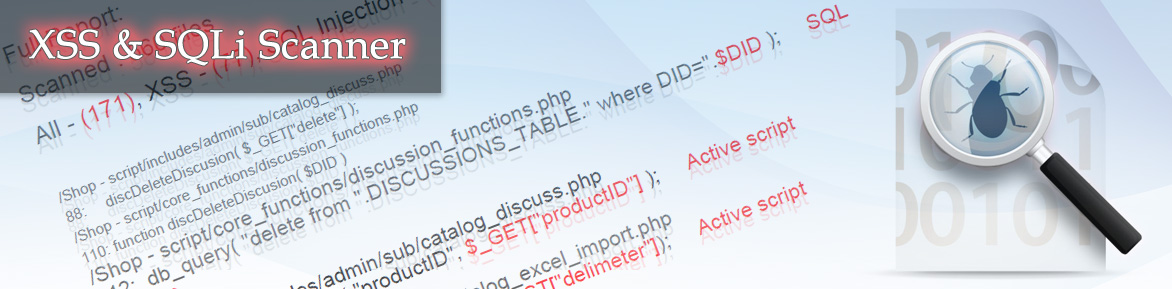
 This tool is designed to help search for XSS and SQL Injection vulnerabilities. This service enables you to check PHP files as well ZIP archives up to 10 mb. The VIP users ( registered users) are provided with a detailed scan report. As a result of the scanner’s work, the name of the file will show up in which a potential vulnerability has been found as well as numbered lines of the insecure code in that file, a vulnerable parameter and the vulnerability type.
This tool is designed to help search for XSS and SQL Injection vulnerabilities. This service enables you to check PHP files as well ZIP archives up to 10 mb. The VIP users ( registered users) are provided with a detailed scan report. As a result of the scanner’s work, the name of the file will show up in which a potential vulnerability has been found as well as numbered lines of the insecure code in that file, a vulnerable parameter and the vulnerability type.





 Scanner
Scanner
