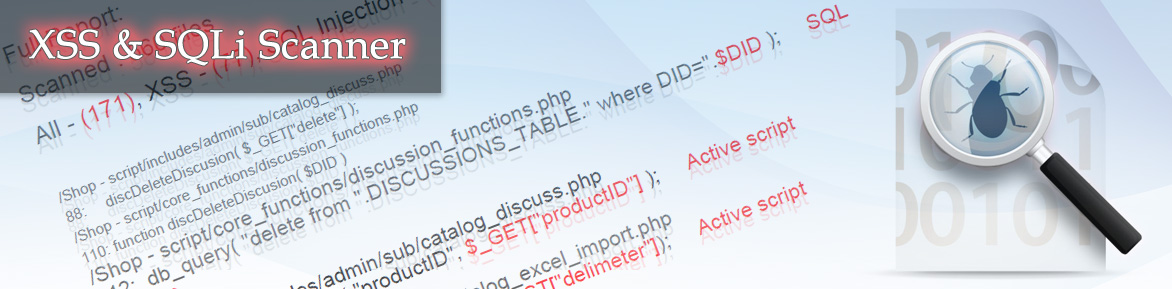
 Our scanner is very popular among site owners whose sites were made in CMS with an open code, which stands to reason. Once one of the owners of such a site used our services and when he found lots of vulnerabilities, somewhat indignant, he wrote about it in the forum of CMS developers. It would have made sense, if the developers had verified the accuracy of the comments, removed the vulnerabilities (we found over 700! XSS vulnerabilities and SQL injections) and thanked their clients for notifying them in a timely way. But CMS developers (whose names we will leave undisclosed) without even taking the trouble to check whether their client was right or not, came to the conclusion that no scanner can possibly find any vulnerabilities. We didn’t try to prove them wrong on the forum. But we feel sincerely sorry for such self-confident developers and even more for their trustful clients. This example was purely educational: don’t repeat his mistake, check your project. What do you have to lose? The scan takes 2 minutes. Maybe you will spend one more minute on opening a file with one of the detected vulnerabilities and verify whether the scanner has made an error or not. Check and see for yourself! Furthermore, one person on another forum suggested that this way we are trying to steal the site’s code. We wonder why would we try to steal the code of an CMS which has an open source code which, moreover, is being distributed on the internet for free? Any way there is a huge amount of freely distributed code on the internet! We declare officially that files are deleted immediately after the scan! And who would need a code without the databases and content? Look at the scan meter and multiply it by the code volume – even physically you can’t look through it in 100 years! Videos, music and pictures are not meant to be run through the scanner. The scanner checks only PHP, HTML and JavaScript files. The only thing we recommend is delete the configuration file of your site before loading the code into the scanner since in it the login and the password to the database are usually stored. We don’t need it but this way you will be absolutely sure that nothing will be stolen from you by the scanner and will be able to sleep peacefully.
Our scanner is very popular among site owners whose sites were made in CMS with an open code, which stands to reason. Once one of the owners of such a site used our services and when he found lots of vulnerabilities, somewhat indignant, he wrote about it in the forum of CMS developers. It would have made sense, if the developers had verified the accuracy of the comments, removed the vulnerabilities (we found over 700! XSS vulnerabilities and SQL injections) and thanked their clients for notifying them in a timely way. But CMS developers (whose names we will leave undisclosed) without even taking the trouble to check whether their client was right or not, came to the conclusion that no scanner can possibly find any vulnerabilities. We didn’t try to prove them wrong on the forum. But we feel sincerely sorry for such self-confident developers and even more for their trustful clients. This example was purely educational: don’t repeat his mistake, check your project. What do you have to lose? The scan takes 2 minutes. Maybe you will spend one more minute on opening a file with one of the detected vulnerabilities and verify whether the scanner has made an error or not. Check and see for yourself! Furthermore, one person on another forum suggested that this way we are trying to steal the site’s code. We wonder why would we try to steal the code of an CMS which has an open source code which, moreover, is being distributed on the internet for free? Any way there is a huge amount of freely distributed code on the internet! We declare officially that files are deleted immediately after the scan! And who would need a code without the databases and content? Look at the scan meter and multiply it by the code volume – even physically you can’t look through it in 100 years! Videos, music and pictures are not meant to be run through the scanner. The scanner checks only PHP, HTML and JavaScript files. The only thing we recommend is delete the configuration file of your site before loading the code into the scanner since in it the login and the password to the database are usually stored. We don’t need it but this way you will be absolutely sure that nothing will be stolen from you by the scanner and will be able to sleep peacefully.
Article





 Scanner
Scanner
