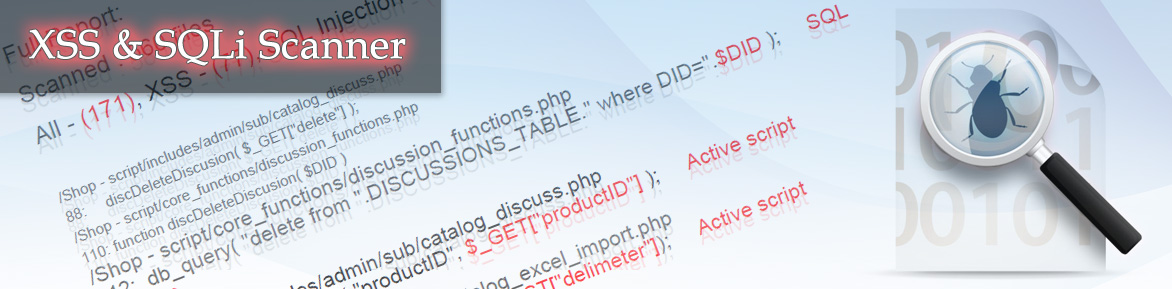
 In the past month the core of the scanner 0.3.0 has been upgraded to 0.3.3. In 0.3.1 and 0.3.2 versions only the core optimization was changed. In the 0.3.3 version some important changes have taken place. In the report interface, the name of the variable which makes the code vulnerable has been added. This is a big help in fixing the problem. The occurrence of Warning statuses is now reduced by 90%. To remind, a Warning status is something that the scanner hasn’t been able to track down but could neither classify it as a safe code. The quantity and the relevance of detected vulnerabilities has increased by 10-20%.
In the past month the core of the scanner 0.3.0 has been upgraded to 0.3.3. In 0.3.1 and 0.3.2 versions only the core optimization was changed. In the 0.3.3 version some important changes have taken place. In the report interface, the name of the variable which makes the code vulnerable has been added. This is a big help in fixing the problem. The occurrence of Warning statuses is now reduced by 90%. To remind, a Warning status is something that the scanner hasn’t been able to track down but could neither classify it as a safe code. The quantity and the relevance of detected vulnerabilities has increased by 10-20%.
About our plans for the subsequent versions:
At this stage we encounter situations when the detected vulnerability is not displayed. For example, a non-screening variable has been transferred into a function and from there into another function and, say, in the fifth function has been used in an sql request. The problem is how to display the report. Since when you see a line with an sql request in the report, it is not quite clear where exactly the vulnerability is to be found. And to track it five functions back to the place where the parameter was obtained is laborious. There are also some points in sql requests.
For example, the following code is vulnerable:
mysql_query("select * from users where id=".addslashes($_GET['id']));
while the one below is not:
mysql_query("select * from users where id='".addslashes($_GET['id'])."'");
We are planning to be able to track such situations in the 0.4.0 version. We are also planning to resolve in it the matter of the report format described above.





 Scanner
Scanner
