Статистика уязвимостей за 2013 год
 Дорогие друзья сайта find-xss.net, как принято в начале нового года мы публикуем статистику найденных уязвимостей нашим сканером. На графике слева на право обозначены:
Дорогие друзья сайта find-xss.net, как принято в начале нового года мы публикуем статистику найденных уязвимостей нашим сканером. На графике слева на право обозначены:
Количество проверок - 29 417
Количество найденных уязвимостей - 242 021
количество проверенного кода - 9 313 мб
Vulnerability statistics for 2012
 Dear users of Find-XSS.net! In this section we offer you to get acquainted with the statistics obtained by scanning our clients’ projects.
Dear users of Find-XSS.net! In this section we offer you to get acquainted with the statistics obtained by scanning our clients’ projects.
Note: we present data for the last two years below.
The question of trust: a Find-Compromise scanner client
 Are you afraid to download the source code in the scanner? We understand you but now you should not worry about it. We have developed a client part of scanner. It works in Java. So if you have not installed the Java virtual machine yet, it’s the time to do it. A Find-Compromise Client will analyze your project on your computer and create a file. The file will have pieces of code which require additional testing, by the server part of the scanner now. After downloading of this file the scanner will give the report. So you will not have to worry about your project, and we - for exclusivity of our product.
Are you afraid to download the source code in the scanner? We understand you but now you should not worry about it. We have developed a client part of scanner. It works in Java. So if you have not installed the Java virtual machine yet, it’s the time to do it. A Find-Compromise Client will analyze your project on your computer and create a file. The file will have pieces of code which require additional testing, by the server part of the scanner now. After downloading of this file the scanner will give the report. So you will not have to worry about your project, and we - for exclusivity of our product.
The first stable version of 1.0.0 Scanner
 A service passed beta testing and switched to the operating mode. And we can surely say that 9 of 10 vulnerabilities found by it exist! This figure is higher than that of any other vulnerability of PHP code scanner. The number of found vulnerabilities is also higher than that of any other PHP code scanner as well as input selection options scanner. The only requirement for scanning is to download the archive which includes all the functions used in the scanned files. The scanner interprets any functions which are not described in a downloadable archive as dangerous. That can cause errors in the report.
A service passed beta testing and switched to the operating mode. And we can surely say that 9 of 10 vulnerabilities found by it exist! This figure is higher than that of any other vulnerability of PHP code scanner. The number of found vulnerabilities is also higher than that of any other PHP code scanner as well as input selection options scanner. The only requirement for scanning is to download the archive which includes all the functions used in the scanned files. The scanner interprets any functions which are not described in a downloadable archive as dangerous. That can cause errors in the report.
A new version of the scanner 0.6.0, what’s new?
 The scanner checks the input data received from the user and analyzes their behavior in the code. The analysis of all functions to determine degree of danger or safety which is used in further analysis of the code is produced. Therefore it is very important not to download separate modules (since they use the functions that are described elsewhere), but the entire site (project) as a whole. Otherwise, scan report may be erroneous. In version 0.6.0 the hidden code generated by the function base64_encode and used in conjunction eval (base64_decode ()); is analyzed. This is an example below:
The scanner checks the input data received from the user and analyzes their behavior in the code. The analysis of all functions to determine degree of danger or safety which is used in further analysis of the code is produced. Therefore it is very important not to download separate modules (since they use the functions that are described elsewhere), but the entire site (project) as a whole. Otherwise, scan report may be erroneous. In version 0.6.0 the hidden code generated by the function base64_encode and used in conjunction eval (base64_decode ()); is analyzed. This is an example below:
The simplest code that an attacker can keep in a template or in some module is as follows:
eval (base64_decode ("JF9HRVRbJ3Rlc3QnXQ =="));
A new version of 0.5.0 scanner and how to use it
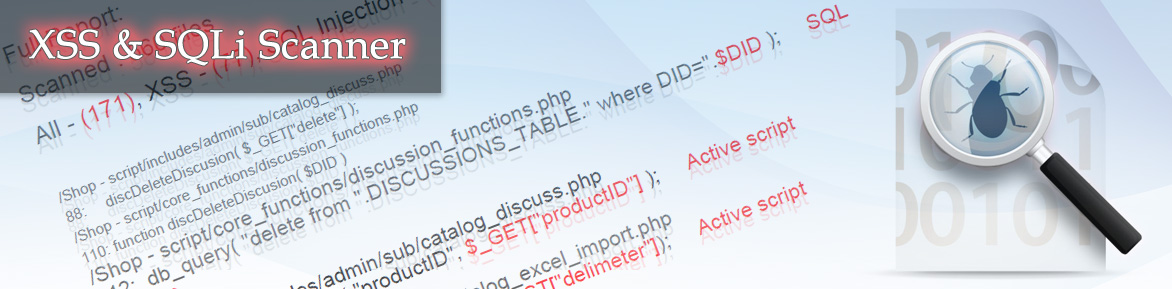
 As it was promised earlier, the status of Warning as well as the status of Error is abolished in a new version of a scanner. Scan report in the new version has changed a lot. Now the report specifies three types of vulnerabilities: XSS, SQL injection and Active script (other vulnerabilities). Scan report in previous versions of the scanner put some in a deadlock, especially vulnerability to the status of Warning. In the new version of scanner everything is done to simplify the understanding of the logic on which the scanner has found a particular vulnerability. The report shows the key lines of code side by side with the vulnerability line. Therefore, we can trace all the chain the scanner used in the analysis. Unsafe option is released in red in the report. For non-experienced website owners, when you hover the mouse on a line with a vulnerability, the prompt with the way to remove appears.
As it was promised earlier, the status of Warning as well as the status of Error is abolished in a new version of a scanner. Scan report in the new version has changed a lot. Now the report specifies three types of vulnerabilities: XSS, SQL injection and Active script (other vulnerabilities). Scan report in previous versions of the scanner put some in a deadlock, especially vulnerability to the status of Warning. In the new version of scanner everything is done to simplify the understanding of the logic on which the scanner has found a particular vulnerability. The report shows the key lines of code side by side with the vulnerability line. Therefore, we can trace all the chain the scanner used in the analysis. Unsafe option is released in red in the report. For non-experienced website owners, when you hover the mouse on a line with a vulnerability, the prompt with the way to remove appears.
Vulnerability statistics for 2011
 The year of 2011 has ended and it is possible to collect and analyze data. When scanning, the scanner logs size of a file, the number of discovered vulnerabilities, there is a counter of scans as well.
The year of 2011 has ended and it is possible to collect and analyze data. When scanning, the scanner logs size of a file, the number of discovered vulnerabilities, there is a counter of scans as well.
Here are the figures for 2011:
The number of scans 13.143, the amount of trusted code 7,122,421,827 bytes, the number of discovered vulnerabilities 35.545.
If you make simple mathematical operations you’ll take 2.7 vulnerability for each scanning. Or, in other words, one vulnerability on every 200.377 bytes of code.





 Scanner
Scanner
