A new version of 0.5.0 scanner and how to use it
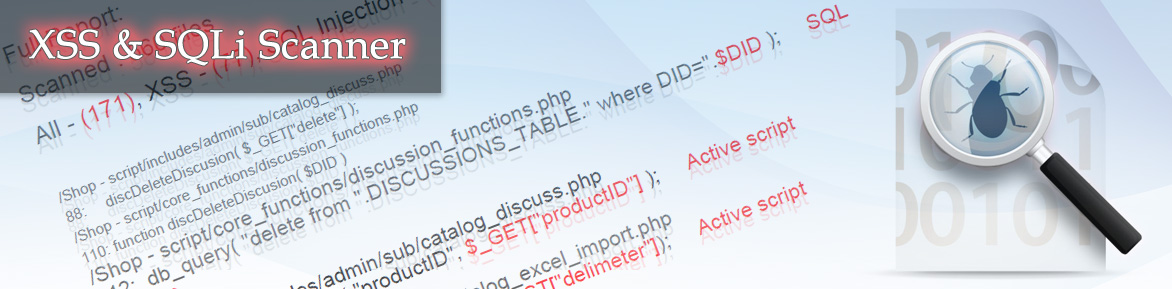
 As it was promised earlier, the status of Warning as well as the status of Error is abolished in a new version of a scanner. Scan report in the new version has changed a lot. Now the report specifies three types of vulnerabilities: XSS, SQL injection and Active script (other vulnerabilities). Scan report in previous versions of the scanner put some in a deadlock, especially vulnerability to the status of Warning. In the new version of scanner everything is done to simplify the understanding of the logic on which the scanner has found a particular vulnerability. The report shows the key lines of code side by side with the vulnerability line. Therefore, we can trace all the chain the scanner used in the analysis. Unsafe option is released in red in the report. For non-experienced website owners, when you hover the mouse on a line with a vulnerability, the prompt with the way to remove appears.
As it was promised earlier, the status of Warning as well as the status of Error is abolished in a new version of a scanner. Scan report in the new version has changed a lot. Now the report specifies three types of vulnerabilities: XSS, SQL injection and Active script (other vulnerabilities). Scan report in previous versions of the scanner put some in a deadlock, especially vulnerability to the status of Warning. In the new version of scanner everything is done to simplify the understanding of the logic on which the scanner has found a particular vulnerability. The report shows the key lines of code side by side with the vulnerability line. Therefore, we can trace all the chain the scanner used in the analysis. Unsafe option is released in red in the report. For non-experienced website owners, when you hover the mouse on a line with a vulnerability, the prompt with the way to remove appears.
Статусы Error и Warning в версии 0.4.7
 Уважаемые пользователи Find-XSS.net, обращаем Ваше внимание на то, что с совершенствованием алгоритма XSS-сканера постепенно изменяется и смысл присваиваемых им статусов. Так, в начальных версиях сканера присутствовал статус Notice, предупреждавший пользователя о существовании возможной опасности. Несмотря на тот факт, что 50% случаев этим предупреждением можно было пренебречь, в последующих версиях сканер стал отслеживать все, что касалось этого статуса. Поэтому мы приняли решение упразднить Notice, оставив только статусы Error и Warning. В предлагаемой Вам обновленной версии (0.4.7) сканера и статус Error, и статус Warning означают наличие уязвимости. Разница между ними заключается лишь в том, что статус Error определяет конкретный тип уязвимости: XSS, SQL injection или же какой-нибудь другой активный код; а статус Warning означает, что во время проверки сканер обнаружил уязвимость SQL injection или XSS в теле функции, и Вам нужно проверить как параметры, получаемые этой функцией, в указанной строке кода, так и их использование в теле функции.
Уважаемые пользователи Find-XSS.net, обращаем Ваше внимание на то, что с совершенствованием алгоритма XSS-сканера постепенно изменяется и смысл присваиваемых им статусов. Так, в начальных версиях сканера присутствовал статус Notice, предупреждавший пользователя о существовании возможной опасности. Несмотря на тот факт, что 50% случаев этим предупреждением можно было пренебречь, в последующих версиях сканер стал отслеживать все, что касалось этого статуса. Поэтому мы приняли решение упразднить Notice, оставив только статусы Error и Warning. В предлагаемой Вам обновленной версии (0.4.7) сканера и статус Error, и статус Warning означают наличие уязвимости. Разница между ними заключается лишь в том, что статус Error определяет конкретный тип уязвимости: XSS, SQL injection или же какой-нибудь другой активный код; а статус Warning означает, что во время проверки сканер обнаружил уязвимость SQL injection или XSS в теле функции, и Вам нужно проверить как параметры, получаемые этой функцией, в указанной строке кода, так и их использование в теле функции.
Find-String Utility, searching lines of code
 When creating a website, you often have to look for one or another piece of code in files. Especially when snapping the template. The problem can be solved if you have a shell and basic knowledge of the grep command. But it is bad if you don’t. The utility is designed for just such occasions. The operational principle of it is extremely simple. Specify which files to scan (only the file extensions, basic ones are by default). Specify the folder to be scanned (all of its subfolders are scanned). And then the string to search. Those who know regular expressions can use them in a mode for regular expressions. For example in such a way /(<a *.*?href=[\'\"]?http[s]?:\/\/.*?<\/a>)+/ you will find files that have external links. And like this - the files that have email-s / [a-z0-9 \.] + @ [A-z0-9 \.] + / I. Examples are indicative, you can write down your own expressions.
When creating a website, you often have to look for one or another piece of code in files. Especially when snapping the template. The problem can be solved if you have a shell and basic knowledge of the grep command. But it is bad if you don’t. The utility is designed for just such occasions. The operational principle of it is extremely simple. Specify which files to scan (only the file extensions, basic ones are by default). Specify the folder to be scanned (all of its subfolders are scanned). And then the string to search. Those who know regular expressions can use them in a mode for regular expressions. For example in such a way /(<a *.*?href=[\'\"]?http[s]?:\/\/.*?<\/a>)+/ you will find files that have external links. And like this - the files that have email-s / [a-z0-9 \.] + @ [A-z0-9 \.] + / I. Examples are indicative, you can write down your own expressions.
Find-Error Utility
 Find-Error Utility is designed to test PHP code for errors. You can say that it is your graphics editor that copes with this task. But using the editor you check file by file, which is for a long time, and is not even real for large projects. The utility will check your entire project at once! The only utility requirement is enabled directive display_errors = On. It is enabled in php.ini. After you enable it restart the server apache. Otherwise, the utility will display only critical errors without Warning and Notice.
Find-Error Utility is designed to test PHP code for errors. You can say that it is your graphics editor that copes with this task. But using the editor you check file by file, which is for a long time, and is not even real for large projects. The utility will check your entire project at once! The only utility requirement is enabled directive display_errors = On. It is enabled in php.ini. After you enable it restart the server apache. Otherwise, the utility will display only critical errors without Warning and Notice.
Find-Port Utility
 Find-Port Utility is designed for checking open ports. It is extremely simple in use. Scanning takes seconds. If you are going to scan a remote site, you need to specify in the code of the utility the target IP address or host name (domain) in line:
Find-Port Utility is designed for checking open ports. It is extremely simple in use. Scanning takes seconds. If you are going to scan a remote site, you need to specify in the code of the utility the target IP address or host name (domain) in line:
$ host = $ _SERVER ['SERVER_ADDR'];
For example, in such a way:
$ host = "example.com";
Find-Link Utility
 As we know almost all the the developers of modules, plugins and CMS, leave direct links to their sites. And sometimes it takes a long time to find external links. Find-Link script is designed for searching the external links. All you need is to copy the script file to the root directory of the site and open it in your browser. The script will show the file in which there is an external link and code. You will only need to remove it.
As we know almost all the the developers of modules, plugins and CMS, leave direct links to their sites. And sometimes it takes a long time to find external links. Find-Link script is designed for searching the external links. All you need is to copy the script file to the root directory of the site and open it in your browser. The script will show the file in which there is an external link and code. You will only need to remove it.
How does it work?
 This tool is designed to help search for XSS and SQL Injection vulnerabilities. This service enables you to check PHP files as well ZIP archives up to 10 mb. The VIP users ( registered users) are provided with a detailed scan report. As a result of the scanner’s work, the name of the file will show up in which a potential vulnerability has been found as well as numbered lines of the insecure code in that file, a vulnerable parameter and the vulnerability type.
This tool is designed to help search for XSS and SQL Injection vulnerabilities. This service enables you to check PHP files as well ZIP archives up to 10 mb. The VIP users ( registered users) are provided with a detailed scan report. As a result of the scanner’s work, the name of the file will show up in which a potential vulnerability has been found as well as numbered lines of the insecure code in that file, a vulnerable parameter and the vulnerability type.





 Scanner
Scanner
